IP Rotation, Anti-Detect Browsers & Account Security: Why Fingerprinting Still Beats You
The Hard Truth About Anti-Detect Browsers and Real Account Security
A freelance marketer, operating multiple client ad accounts, thought he had mastered the art of stealth. With a rotating proxy service and regularly switched IPs, he believed platform algorithms would never catch him. But one morning, three of his Facebook ad accounts were banned simultaneously.
No warnings. No chance to appeal.
He had relied solely on IP rotation for security. But in doing so, he ignored the invisible giveaway: browser fingerprinting.

This is the mistake thousands make every day.
Despite advances in anti-detect browser technologies and proxy integration, account bans are increasing.
Why?
Because too many still believe in surface-level disguise. But Account Security in 2025 is no longer about just changing your IP—it's about mastering the full digital identity stack: from device fingerprinting to browser isolation, and most importantly, binding IP to behavior.
The Misguided Faith in IP Rotation Alone
Many still equate IP rotation with anonymity.
The logic is simple: different IP = different user.
But platform algorithms today are far more sophisticated. IP is just one layer in a much larger identity fingerprint.

Problem 1: Low-quality proxies & IP range overlap
Many proxy services reuse limited IP pools. If two users happen to operate on the same subnet or ASN, systems like Meta or Google immediately flag them as suspicious.
Shared or datacenter proxies are especially vulnerable
IPs flagged in previous abuse patterns get recycled
IP rotation, in this case, simply rotates the danger.
Problem 2: DNS leaks & time zone inconsistencies
Switching IPs does little if your DNS requests still route through your local ISP or if your browser time zone doesn't match the new IP's geolocation. Platforms catch on quickly.
Leaked DNS = real location exposure
Time zone + language mismatch = automation signal
Problem 3: Multi-account management creates invisible threads
Running multiple accounts without proper browser isolation creates invisible behavioral trails:
Shared cookies
Similar navigation patterns
Overlapping login times
Even with fresh IPs, these patterns give away the connection.
This is the fatal flaw of relying solely on proxies. The system sees more than your IP.
The Real Anatomy of Digital Disguise
Shield 1: Intelligent IP Rotation
Let’s not dismiss IP rotation completely—it’s still essential. But only if:
The IPs are from residential or mobile pools
The rotation pattern mimics human behavior
The proxy settings are correctly embedded in the browser, avoiding leaks.
High-quality IPs aren’t just about location. They’re about history, consistency, and credibility.
Shield 2: Fingerprint and Environment Spoofing
Browser fingerprinting goes far beyond user agents. Advanced tracking scripts capture:
Canvas and WebGL rendering
Installed fonts and extensions
Audio stack behavior
WebRTC signals
Device screen resolution and color depth
To stay hidden, you must spoof or randomize these at runtime. This is the foundation of anti detect browser architecture.
Shield 3: IP-Environment Binding
Here's the overlooked principle: security comes from consistency, not chaos.
Each IP should be bound to an environment—time zone, language, hardware profile, and behavioral patterns must align. This creates a digital persona that platforms recognize as "real."
Don’t rotate identities randomly. Bind environments to accounts. That’s true stealth.

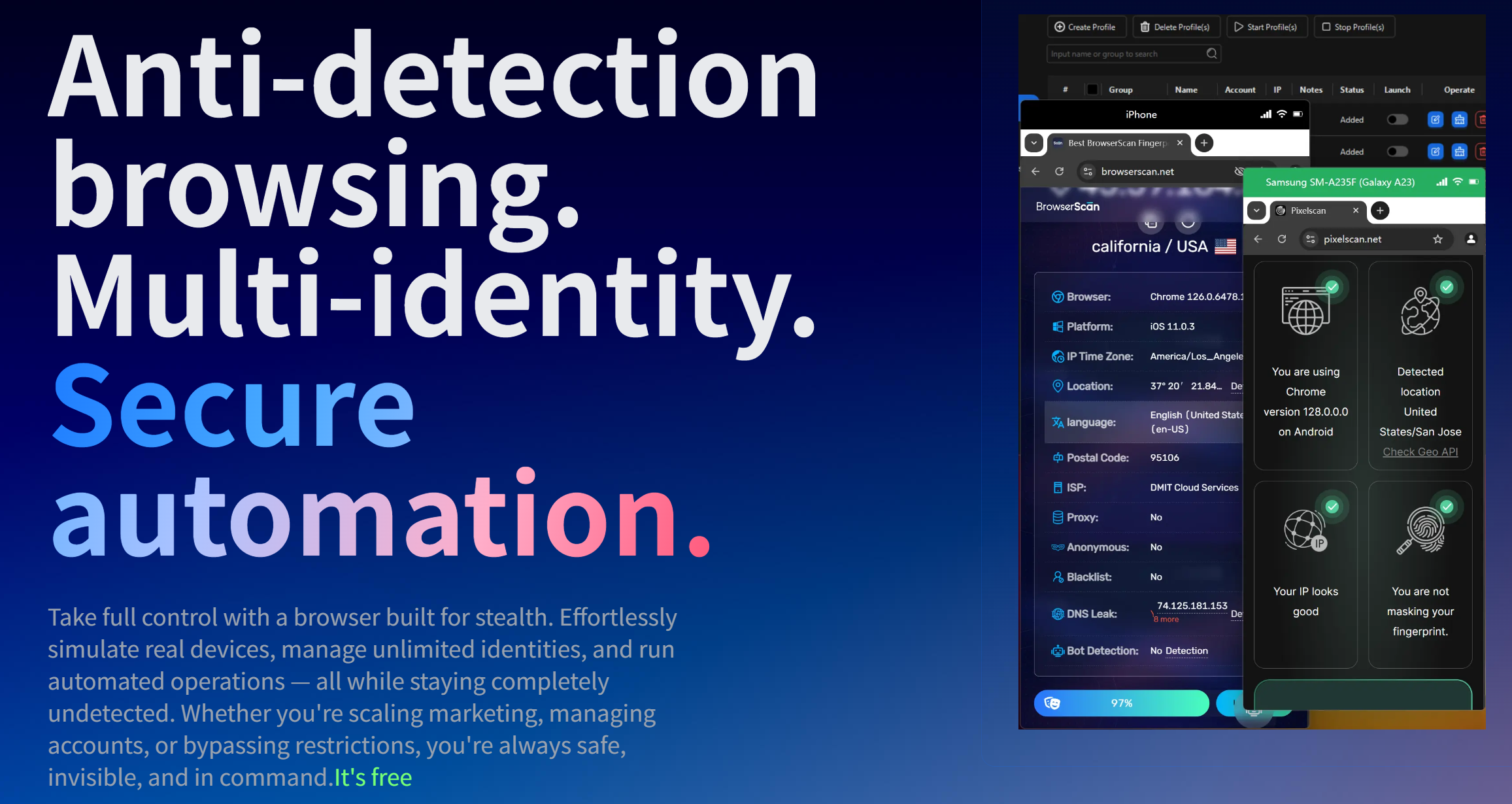
The MultiLoginPro Protocol
Layer 1: Integrated IP + Proxy Sync
Syncs proxy configuration directly into your browser environment
Ensures DNS, WebRTC, and geo settings match IP
Supports residential and mobile proxy providers with automated health checks
Layer 2: Dynamic Device Fingerprinting
Realistic emulation of hardware + software stack
Generates unique browser fingerprints per profile
Prevents detectable duplication across sessions
Layer 3: Persistent Identity Engine
Each account gets a persistent, isolated browser container
No shared cookies, storage, or device signals
Profiles simulate long-term user behavior
Together, these three layers form a system-level camouflage: a deepfake of a real person that platforms accept.
Environment Binding: A New Paradigm for Digital Identity
Too many people still treat proxies as masks they can wear and discard. But digital platforms don’t track masks. They track habits.
Constant IP changes without behavioral consistency = red flag
Disconnected time zones = bot pattern
Environment reset on every login = untrustworthy
What environment binding gets right? Environment binding means assigning:
One IP + browser + device fingerprint
One location + timezone + behavior profile
One unique path of digital identity
To each account. Always.
This creates a believable device fingerprinting narrative that holds up under scrutiny.
Use Cases That Demand System-Level Stealth
1. Telegram/WhatsApp Account Creation
These platforms block entire subnets and monitor fingerprint anomalies:
SIM-based verification gets wasted with weak proxies
Inconsistent environments trigger bans even post-verification
MultiLoginPro solves this with:
Mobile proxy sync
Clean environment simulation
Consistent fingerprint locking
2. Facebook Ad Account Operations
Platform tracks IP reputation, cookies, canvas, WebRTC, more
Multiple ad accounts from same environment = instant suspension
With MultiLoginPro:
Each ad account runs in a sandboxed environment
Fingerprints and IPs remain unique and consistent
Marketers avoid bulk bans while scaling operations
Real Team, Real Result
A growth marketing team of 7 manages over 200 Facebook and TikTok ad accounts using MultiLoginPro.
Each member operates 25-30 accounts
IPs are bound to unique fingerprinted environments
Proxy rotation is handled through mobile providers with full DNS and WebRTC shielding
In 14 months:
Zero bans due to fingerprint or proxy detection
CTR and ROAS metrics outperform manual account operations
Account lifespan extends by 3-5x
Proof that proxy integration, when done right, supports scale without sacrifice.
Don’t Just Change Your IP
The age of IP-based security is over.
True account security now depends on:
Accurate device fingerprinting
Realistic environment simulation
Binding IPs to behavior, not just browsers
Browser isolation and anti-detect browser technology are no longer optional—they’re foundational. Platforms are smarter, and users must evolve.
If you’re still relying on random IP rotation, you’re not invisible. You’re just exposed with a different address.


